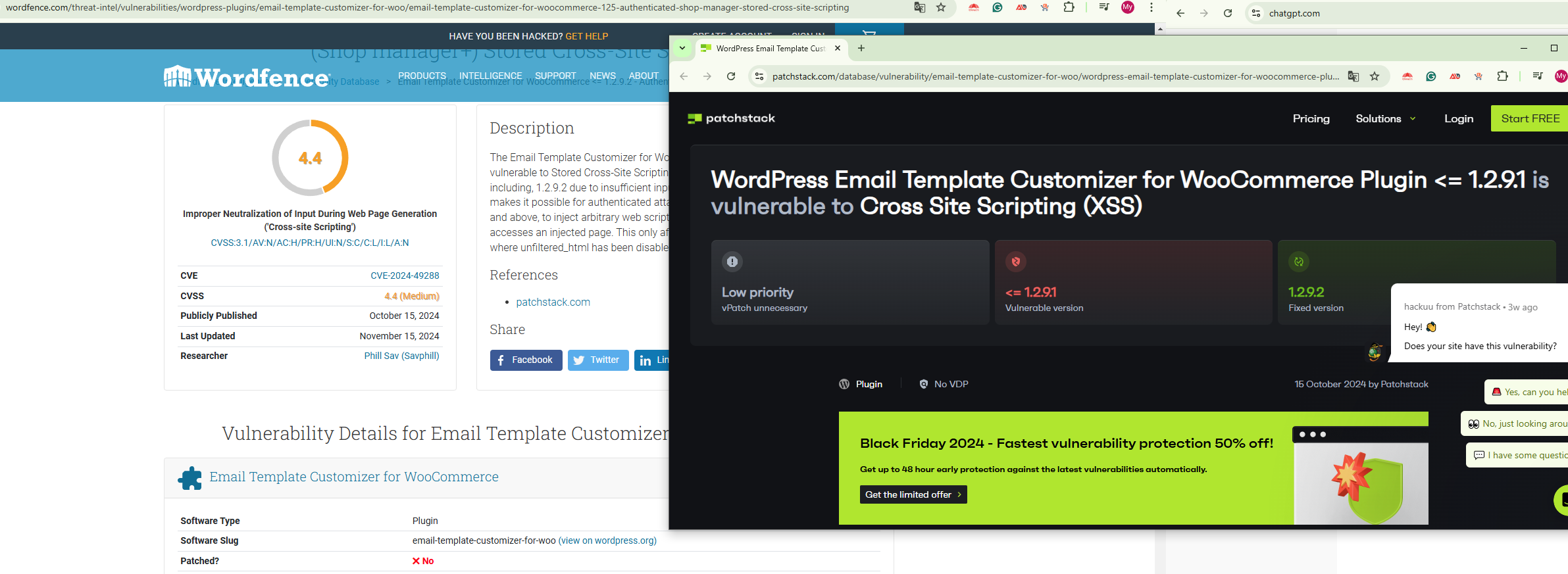
Latest update has vulnerability reported by Wordfense
-
Good morning
Wordfense has reported a vulnerability from your latest update – info copy and pasted from their report below:
The Email Template Customizer for WooCommerce plugin for WordPress is vulnerable to Stored Cross-Site Scripting via admin settings in all versions up to, and including, 1.2.7 due to insufficient input sanitization and output escaping. This makes it possible for authenticated attackers, with shop manager-level permissions and above, to inject arbitrary web scripts in pages that will execute whenever a user accesses an injected page. This only affects multi-site installations and installations where unfiltered_html has been disabled.
- You must be logged in to reply to this topic.