logs shows threat from whitelisted ipv6.
-
I have both ipv4 and ipv6 for my domain. I still get threats from my own ipv6 address even though I have whitelisted the ipv6. Also, my website is behind Cloudflare.
logs:
13/Jul/21 22:09:14 #2870588 MEDIUM - 2503:f198:5:107b::ac5:7033 POST /wp-admin/admin-ajax.php - Blocked access to admin-ajax.php - [bot detection is enabled] - www.gadgets96.com 13/Jul/21 23:43:32 #8738977 HIGH - 2503:f198:5:107b::ac5:7033 GET /index.php - User enumeration scan (author archives) - [author_name=gadgets96_tuhjqb] - www.gadgets96.com.htninja:
if ( $_SERVER["REMOTE_ADDR"] == '2503:f198:5:107b::ac5:7033' ) { return 'ALLOW'; // whitelist }
-
If you’re behind Cloudflare, did you add this code to your .htninja:
https://www.ads-software.com/support/topic/http_cf_connecting_ip/It must be on top of the file, before any other code that deals with IP addresses.
Yes, I have added those codes in the .htninja file. See the full code in ninja file below:
<?php /* +=====================================================================+ | NinjaFirewall optional configuration file | | | | See: https://nintechnet.com/ninjafirewall/wp-edition/help/?htninja | | | +=====================================================================+ */ // To tell NinjaFirewall where you moved your WP config file, // use the '$wp_config' variable : // ** NOTE: Deprecated since NinjaFirewall 3.0.1 ** // $wp_config = '/foo/bar/wp-config.php'; // Users of Cloudflare CDN: if (! empty($_SERVER["HTTP_CF_CONNECTING_IP"]) && filter_var($_SERVER["HTTP_CF_CONNECTING_IP"], FILTER_VALIDATE_IP) ) { $_SERVER["REMOTE_ADDR"] = $_SERVER["HTTP_CF_CONNECTING_IP"]; } // Users of Incapsula CDN: // if (! empty($_SERVER["HTTP_INCAP_CLIENT_IP"]) && // filter_var($_SERVER["HTTP_INCAP_CLIENT_IP"], FILTER_VALIDATE_IP) ) { // $_SERVER["REMOTE_ADDR"] = $_SERVER["HTTP_INCAP_CLIENT_IP"]; // } // Whitelist/blacklist whatever you want: // // Return codes: // 'ALLOW' == Allow and stop filtering (whitelist). // 'BLOCK' == Reject immediately (blacklist). // // Any other return code will be ignored // // Note that if you use 'ALLOW'/'BLOCK', nothing will be written // to the firewall log. // ======================================================= // Whitelist single IP ipv6 - 2503:f198:5:107b::ac5:7033: if ( $_SERVER["REMOTE_ADDR"] == '2503:f198:5:107b::ac5:7033' ) { return 'ALLOW'; // whitelist } // Allow JetPack CIDR (IPv4 **only**): $cidr_array = array('192.0.64.0/18'); // Loop through the array: foreach ( $cidr_array as $cidr ) { // Check IP vs CIDR: if ( ipCIDRCheck( $_SERVER['REMOTE_ADDR'], $cidr ) ) { // IP matches, allow it: return 'ALLOW'; } } function ipCIDRCheck( $IP, $CIDR ) { list ( $subnet, $bits ) = explode( '/', $CIDR ); $ip = ip2long( $IP ); $subnet = ip2long( $subnet ); $mask = -1 << ( 32 - $bits ); $subnet &= $mask; return ( $ip & $mask ) == $subnet; } // ======================================================= // Whitelist IPs 1.1.1.1, 2.2.2.2 and 3.3.3.3: // $ip_array = array( '1.1.1.1' , '2.2.2.2' , '3.3.3.3' ); // if ( in_array( $_SERVER["REMOTE_ADDR"], $ip_array ) ) { // return 'ALLOW'; // whitelist // } // Whitelist all IPs from 1.1.1.1 to 1.1.1.255: // if ( preg_match( '/^1\.1\.1\.\d+$/', $_SERVER["REMOTE_ADDR"] ) ) { // return 'ALLOW'; // whitelist // } // Blacklist single IP 1.2.3.4: // if ( $_SERVER["REMOTE_ADDR"] == '1.2.3.4' ) { // return 'BLOCK'; // blacklist // } // Blacklist IPs 1.1.1.1, 2.2.2.2 and 3.3.3.3: // $ip_array = array( '1.1.1.1' , '2.2.2.2' , '3.3.3.3' ); // if ( in_array( $_SERVER["REMOTE_ADDR"], $ip_array ) ) { // return 'BLOCK'; // blacklist // } // Blacklist all IPs from 1.1.1.1 to 1.1.1.255: // if ( preg_match( '/^1\.1\.1\.\d+$/', $_SERVER["REMOTE_ADDR"] ) ) { // return 'BLOCK'; // blacklist // } // Do not filter any HTTP request sent to a script located inside the /myfolder/ directory: // if (strpos($_SERVER['SCRIPT_FILENAME'], '/myfolder/') !== FALSE) { // return 'ALLOW'; // } // Advanced filtering : // Block immediately a POST request if it contains a 'whatever' variable // sent to a script named 'script.php' : // if ( isset($_POST['whatever']) && strpos($_SERVER['SCRIPT_NAME'], 'script.php') !== FALSE ) { // return 'BLOCK'; // } // do not add anything below this line.That looks fine to me.
If you log out of WordPress, then try to access
https://your-site.com/?ninjatest=%00, are you blocked or not?Do you have another instance of NinjaFirewall running in a parent directory for instance?
-
This reply was modified 3 years, 8 months ago by
nintechnet.
Yes, I think, I am blocked. I get an Internal Server Error. Nothing appeared on the logs. But I am surprised, I was expecting a 403 forbidden error. Is there anything wrong?
Do you have another instance of NinjaFirewall running in a parent directory for instance?
I have installed the plugin once from the WordPress repository. That’s it. No other instance running.
-
This reply was modified 3 years, 8 months ago by
praveen369gen.
It looks like you may have another security application on the server. Maybe mod_security?
Try another attempt like this one while you are logged out:https://example.com/?foo=/thrive/krakenThis time I was blocked with the following message with a ninja firewall logo.
Sorry 117.196.167.205, your request cannot be processed. For security reasons, it was blocked and logged.The block was also logged.
16/Jul/21 15:31:01 #1035778 CRITICAL 1408 117.186.157.215 GET /index.php - WP Vulnerability - [SERVER:REQUEST_URI = /?foo=/thrive/kraken] - www.gadgets96.comIt looks like you may have another security application on the server. Maybe mod_security?
Yes, I think so. In my hosting panel, their an option to enable/disable security which I think is mod security. Do you want me to confirm this with the hosting provider?
-
This reply was modified 3 years, 8 months ago by
praveen369gen.
That’s fine. But your IP doesn’t match the one you whitelisted.
Can you try again, but this time with the IP you added to the .htninja so that we can see if the firewall will not block you?Do you mean the ipv6 IP?
It seems like there is some misunderstanding. Actually, the ipv6 IP is my domain’s IP (AAAA Record). I get threat logs from my own domain’s ipv6. I guess it’s the hosting provider messing with the URL so I decided to whitelist the ipv6. Even though I have whitelisted the ipv6, I still get threats logs.
I forget to mention that the IP in the .htninja is not my genuine ipv6 address, It’s a dummy IP. I am not sure if it’s a good idea to share the IP and domain public when I am using Cloudflare reverse proxy to hide my original IP. If you want I can share it with you.
No need to post your real IP, but can you check again and make sure the IP in the .htninja is correct. There could be a mistake or typo for instance.
I double-checked the IP, there aren’t any typos. That’s exactly how I whitelisted IP in my .ninja file.
// Whitelist single IP dreamhost ipv6 - 2507:f258:0005:103b:0000:0000:0ac7:7231: if ( $_SERVER["REMOTE_ADDR"] == '2507:f258:5:103b::ac7:7231' ) { return 'ALLOW'; // whitelist }The IP in the above code is a dummy IP, but no typos.
Can you confirm that the firewall detects and loads the .htninja?
Go to NinjaFirewall > Dashboard and you should see something similar to this:
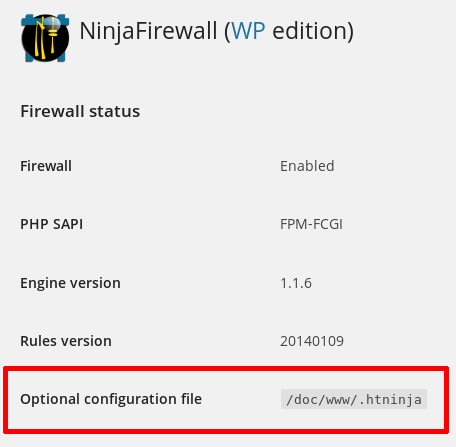
Yes, the firewall has detected and successfully loaded the ninja firewall.
It’s all good. That’s very odd that it’s not working.
Can you try to whistelist your own IPv4 IP address by adding it to the .htninja (below the Cloudflare’s code), then log out of WordPress and try again to access
?foo=/thrive/krakento see if it will not block you?Can you try to whistelist your own IPv4 IP address by adding it to the .htninja
I whitelisted my own IPv4 address and accessed ?foo=/thrive/kraken. It allowed me in. No forbidden message and nothing in the logs.
After some tweaking in my modem, I have somehow enabled IPv6 only mode. Then I whitelisted my own current IPv6 address. Then I tried to access ?foo=/thrive/kraken but nothing happened. Same as the IPv4.
But if tried to access /wp-json/jetpack/v4/scan I get following json and threat log.
json:
{"code":"nfw_rest_api_access_restricted","message":"Forbidden access","data":{"status":403}}log:
21/Jul/21 00:20:19 #4194598 HIGH - 2001:4590:4b75:a569:51fb:4387:d449:ff45 GET /index.php - WordPress: Blocked access to the WP REST API - [/wp-json/jetpack/v4/scan]Later, I disabled the IPv6 and enabled IPv4 in my modem and again whitelisted my own IPv4 then I accessed /wp-json/jetpack/v4/scan. For IPv4, it returned 403 status as in the above json but not logged. That’s is very strange.
-
This reply was modified 3 years, 8 months ago by
praveen369gen.
-
This reply was modified 3 years, 8 months ago by
praveen369gen.
-
This reply was modified 3 years, 8 months ago by
praveen369gen.
Try to add the
NFW_UWLconstant to the .htninja:// Whitelist single IP dreamhost ipv6 - 2507:f258:0005:103b:0000:0000:0ac7:7231: if ( $_SERVER["REMOTE_ADDR"] == '2507:f258:5:103b::ac7:7231' ) { define('NFW_UWL', true); // Force whitelist return 'ALLOW'; // whitelist } -
This reply was modified 3 years, 8 months ago by
- The topic ‘logs shows threat from whitelisted ipv6.’ is closed to new replies.